
find pic here: https://unsplash.com/photos/NIJuEQw0RKg
Introduction to Audit Policies
Audit policies in Imperva DAm enable an organization to monitor access attempts and activity on sensitive data or other data of interest. These policies can be designed to enable an organization to comply with the requirements of data protection regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) or the California Consumer Privacy Act (CCPA), and to perform the monitoring necessary for cybersecurity and breach protection.
Think of audit policies like a DVR (digital video recorder). You may have 400 channels on your satellite or cable system, but you really only like to watch a few channels or shows on it. So you record those shows so you can watch them later. Audit policies act the same way. You record the user activity on those databases that are really important to you so you can rewind and watch that activity later.
Configuring an Audit Policy
An audit policy in Imperva DAM is designed to monitor sensitive information that has already been identified and tracked within the system. Before starting on configuring an audit policy, it is necessary to develop a site tree and to perform a scan for sensitive information.
Determine Policy Requirements
The first step in creating an audit policy is determining the desired goals of the policy. Audit policies can have a number of different applications and may be based upon both internal policies or the requirements of data protection regulations.
Determining the requirements of the audit policy is vital to selecting and configuring the right type of policy. Different regulations cover different types of sensitive data (such as payment card data for PCI DSS and healthcare information for HIPAA) and may require different levels of visibility and data collection for compliance. Identifying these requirements in advance enables an organization to balance the need for visibility with the resources required to store and process the events generated by the audit policy.
Watch the entire Imperva DAM Deployment webinar
Select or Build Audit Policy
Once the requirements of the audit policy have been defined, it is possible to create the policy itself. To do so, select the Policies tab in the top window of the Imperva DAM console, then select the Audit tab in the blue ribbon below.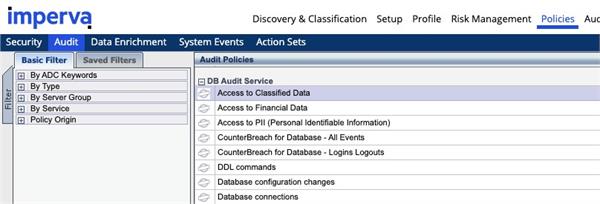
Imperva DAM includes pre-built policies for common regulations such as PCI DSS and SOX. It also has built-in policies for certain types of monitoring actions, such as watching access attempts to sensitive parts of databases or all sensitive information discovered within a scan.
Organizations may have unique monitoring needs, so Imperva DAM also offers the capability to build custom audit policies. These can cover regulations not supported by default or allow an organization to monitor specific types of data in alignment with business needs.
Based on the assessment of policy requirements, it should be possible to identify the pre-built or custom policies that an organization requires. The specific criteria used to identify events of interest can be tuned within the Match Criteria tab of the pane to the right of the screen.
This is why it is so important to start out right with DAM and build a usable site tree. When configuring audit and other policies, monitoring and protection can rapidly be applied to all or a subset of a site in a usable and meaningful way.
Settings Tab
One important configuration setting is the Extended Collection setting. For this setting, it is best to select the Events option. This will provide information about the query, the number of records returned from the database, the types of information returned, etc.