Cross System Global Objects
Welcome to part 6 of our Fundamentals blog series. In this blog, will be looking at defining the Cross System Global objects, what they help you achieve and how to implement them. Be sure to check out the previous blogs in the series - links are included at the end of this blog.
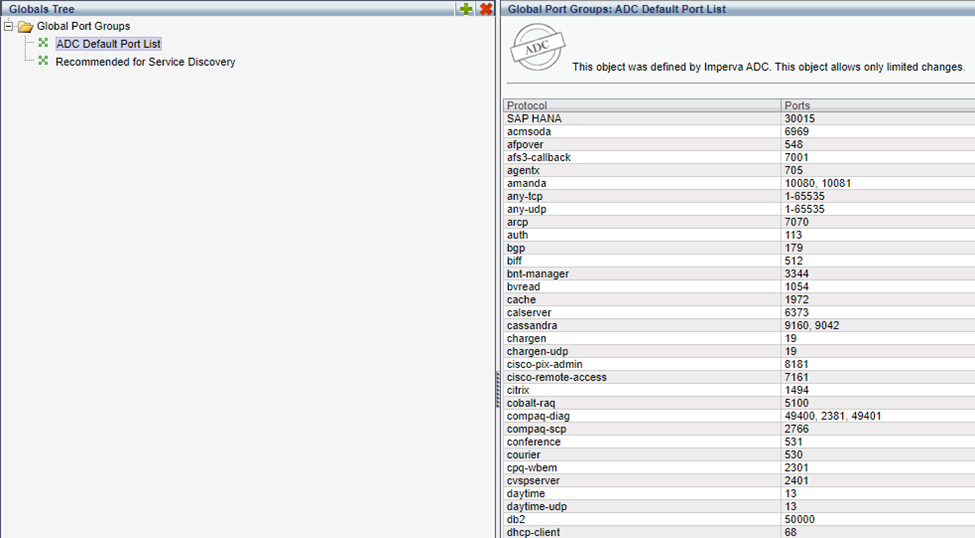
Global Port Groups
Global Port Groups are lists of ports used in various locations in On-Prem WAF, including:
- Service Scans
- Firewall Policy
The Global Ports Group attaches a name to the port number, making it more readable in alerts.
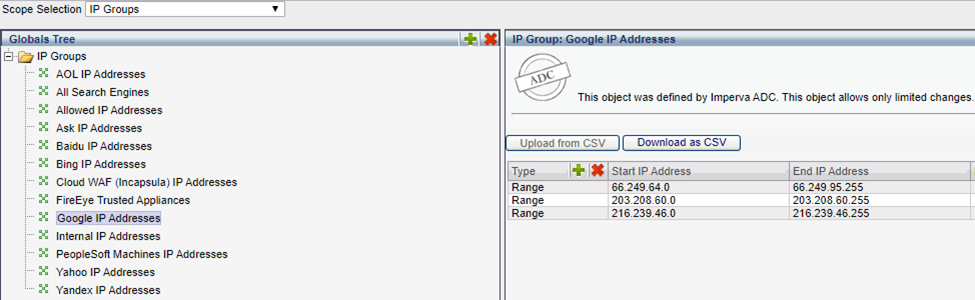
IP Groups
IP Groups are lists of IP Addresses used for a variety of purposes in On-Premises WAF such as monitoring, discovery, allow listing, and Deny listing.
For example, you can exclude the “All Search Engines IP” group from monitoring, to ignore traffic from these addresses as typically, popular search engine traffic can be considered safe.
Port Names
Port Names is a default list that determines all ports that are identified by On-Premises WAF. They determine ports used during discovery when applicable, and are used with the firewall policy.

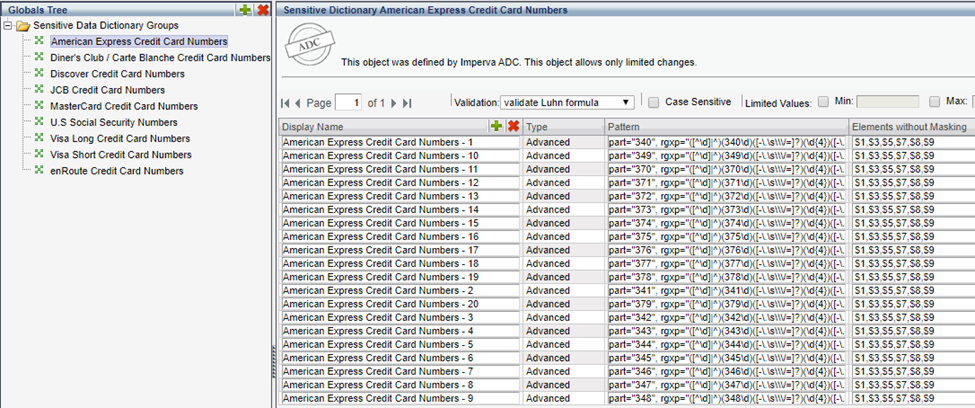
Sensitive Data Dictionary Groups
Sensitive Dictionaries define the data patterns to identify in traffic, then take action. They detect sensitive data such as social security numbers and credit card numbers, and then automatically mask this data.
When attached to a policy, they trigger the policy when detected, and can also be added to database services on the Operation tab to automatically mask this data when detected.
Sensitive Data Dictionary Groups define data by using regular expressions. They mask all data displayed in On-Premises WAF except those specified as elements without masking.
Web Related Global Objects
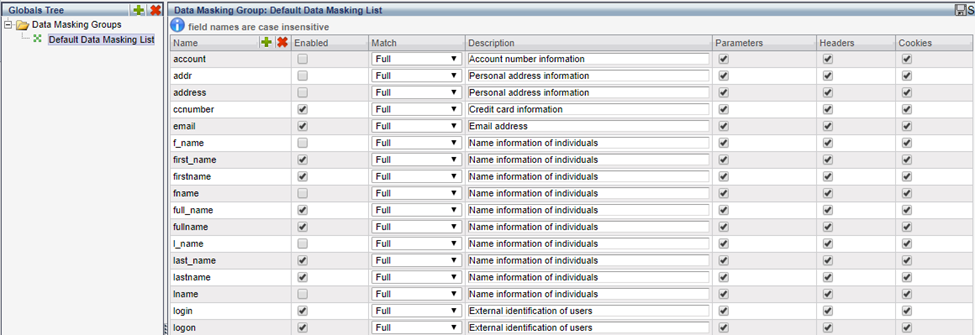
Data Masking Groups
Data Masking Groups define what objects in web traffic to mask in On-Premises WAF. Traffic that is masked then appears in On-Premises WAF alerts, reports, etc., as a series of asterisk (***).
Masking is defined by field name. You then decide when to mask these field names, and whether to mask them when they appear as parameters, in headers, or in cookies. The Data Masking group needs to be attached to the relevant web service on the Operation tab under Data Masking.
File-Type Groups
A File type group is a list of static file types that do not pose a threat to the network or data. It is used to ignore static files which don’t need monitoring. This includes all web server files that don’t involve server activity.
On-Premises WAF comes with a default File Types Group global objects with files to ignore. Once configured, it is attached by selecting the relevant web service, clicking the operation tab, expanding the Restrictions option, and selecting it from the Ignore Static files dropdown list.
Parameter Groups
Parameter Groups define lists of static parameters determined as not posing a threat. They are then used to exclude these elements from monitoring in On-Premises WAF.
Once configured, the group is attached by selecting the relevant web service, clicking the operation tab, expanding the Restrictions option, and selecting it from the Ignore Parameters drop down list.
SOAP Elements
SOAP is the XML-based protocol used for data interchange between applications over HTTP. The SOAP elements global object is a list of SOAP elements determined as not posing a threat to your network or data. It is used to exclude these elements from monitoring.
Once configured, the group is attached by selecting the relevant web service, clicking the operation tab, expanding the Restrictions option, and selecting it from the Ignore SOAP Elements dropdown list.
Parameter Type Configuration
The Parameter Type Configuration global object defines lists of parameters and rules to enforce a complex format when parameters are received as part of web traffic. You can create new types with regular expressions, then add to a profile.
Session Identifier Groups
Session Identifiers are cookie names based on which On-Premises WAF tracks web traffic. Using session identifiers rather than IP addresses to track sessions provides more accurate tracking. Session identifiers are also used for user tracking and session based occurrence counting.
It is important to note, that the most common reason why user tracking doesn’t work is because Session Identifier groups are not properly configured and applied.
Susceptible Directory Groups
Susceptible Directory Groups are a list of directories susceptible to zero-day web worm attacks. They enable the configuration of profiles and policies to identify groups as susceptible and provide tighter access control. Additionally, when a susceptible folder is protected, it cannot be deleted from the profile.
On-Premises WAF comes with a list of predefined susceptible directories. You can create a new list, and add directories to it. They are then protected by the Web Profile which can be seen by accessing the profile, clicking a webpage, and from the Display button, clicking Susceptible Directories.
URL Prefixes Directories Groups
URL Prefixes Directories Groups define a group of URL prefixes or directories. This group is then attached to a web application and used to restrict monitoring to these URLs, or exclude these URLs from monitoring.
You create a directories group, and then add it to the relevant Web application on the Definitions tab, under Restrictions, either restricting Monitoring to these URLs, or ignoring them.
Have a question? We’d love to hear from you - please comment below.
Check out the other blogs in this series below…
Advanced Web Security Policies – Fundamentals of On-Prem WAF Part 5
Types of Web Security Policies - Fundamentals of On-Prem WAF Part 4
Application Hierarchy: Server Group, Service, Application - Fundamentals of On-Prem WAF - Part 3
SSL certificates and Ciphers - Fundamentals of On-Prem WAF - Part 2
Fundamentals of On-Premise WAF - Blog Series Pt1
Or watch our videoseries on WAF Gateway Deployment with Craig Burlinghame
|