
Data Security Risk Reduction
Data breaches are becoming increasingly common. In many cases, these breaches are carried out by external threat actors that take advantage of web application vulnerabilities or other holes in an organization’s cyber defenses.
However, this is not always the case. In some cases, data breaches are carried out (intentionally or not) by trusted insiders. Employee negligence is a growing cause of data breach as mistakes by an employee make it easier for sensitive internal data to be publicly leaked.
Imperva Data Risk Analytics (DRA) can help an organization to reduce its data security risks by providing improved visibility into database access. This can help to identify abuse of database service accounts and suspicious access attempts for application data, two of the most common sources of data security risks.
Database Service Account Abuse
Database service accounts are designed for application usage. Rather than creating an array of user accounts for the database, this enables access control to be abstracted away from the database level.
These database service accounts have a number of different features that pose a serious threat to data security, including:
- High and broad privilege levels
- Unchanging passwords
- Lack of visibility into particular user taking an action with the account
Abuse of database service accounts exists when human users are making use of this account that was designed for applications. Under these circumstances, a large number of people have knowledge of the credentials used by a highly-privileged account with low security visibility. This increases the probability that an attacker will be able to learn these credentials and use them to access and exfiltrate an organization’s sensitive data.
Identifying Database Service Account Abuse with Imperva DRA
Credential sharing is a common threat to enterprise security. A recent survey revealed that 69% of employees admit to sharing credentials with their coworkers. When working with databases, the appeal of sharing access to a service account - which enables employees to perform database actions without requiring individual user accounts - is high.
However, this activity places the organization at risk since the probability of credential compromise is higher. Additionally, incident detection and response is more complicated since the security team lacks the ability to determine which user took a certain action on the database.
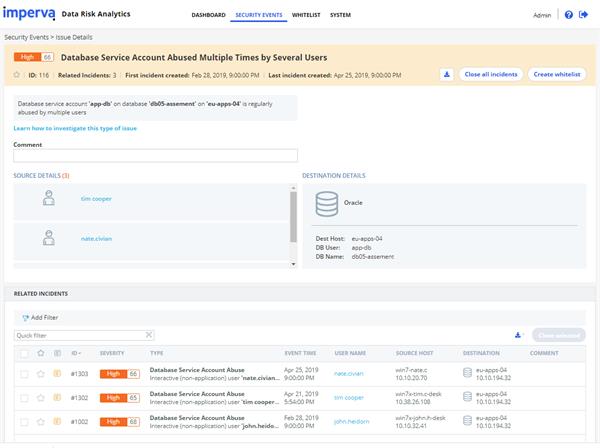
Imperva DRA helps to solve this issue by providing visibility into abuse of database service accounts. The image above shows investigation of an issue in the DRA console relating to this particular type of incident.
As shown in the image, Imperva DRA is capable of identifying the individual users that have been using the database service account. This breakdown of usage provides the visibility needed to determine the scope of the incident, block access of these users to the database service account, and investigate usage to determine if an unauthorized user has accessed the account and used it for data exfiltration.
Suspicious Application Data Access
Many databases are designed to primarily be used by applications. Whether providing access to account data to customers via a web portal or powering an organization’s internal applications, these databases are not intended to be queried directly by human users.
However, the fact that a database is not intended for human usage does not mean that human users do not have access to the data stored in these databases. Database administrators (DBAs) and developers often have a high level of permissions for the company database. While this enables them to perform their job duties, it can also put the organization at risk.
These elevated permissions make DBAs a primary target of cybercriminals. Since their account credentials provide complete access to the data stored within a company database, a successful phishing or other credential-stealing attack enables an attacker to achieve their objective of accessing and stealing sensitive company data.
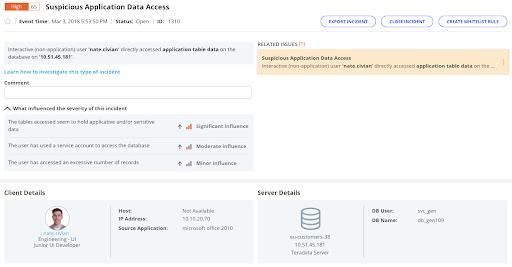
Identifying Suspicious Application Data Access with Imperva DRA
The ability to differentiate human database users from automated ones is a valuable one for incident detection and response. Recently, an organization detected a data breach that had been ongoing for multiple years based upon a database query requesting information regarding the structure of the database. Since the automated programs authorized to access the database would not have made such a request, the anomalous action triggered incident response activities that uncovered the ongoing breach.
Imperva DRA provides an organization with vital visibility into how their databases and the sensitive data that they contain are being used by applications and human users alike. With DRA, an organization can monitor for and respond to the following signs that suspicious application data access is occurring:
- Bulk copying of data from the database
- “Humanlike” queries for an application database
- Database queries using free-form database tools (such as SQL*Plus)
- Access to high-risk or sensitive database tables
In some cases, these “suspicious” access patterns may be legitimate. For example, unusual copying may be performed to set up a backup database or humans may perform certain manual queries as part of testing or troubleshooting. However, the high level of permissions associated with DBA and developer accounts means that unusual activities associated with these accounts warrant investigation.
Imperva DRA Reduces Data Security Risks
A breach of sensitive customer data can cause damage to an organization in a number of different ways. A data breach is likely to result in legal fees and potential penalties under the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and similar data privacy laws. Additionally, a breach is likely to cause a loss of customers or sales and to require significant expenditure to correct brand damage.
Imperva DRA enables a security team to decrease the security risks associated with the sensitive data stored in their databases. The increased visibility that it provides enables detection of dangerous behaviors by privileged database users and abuse of potentially compromised accounts. In combination with SecureSphere, DRA allows a security team to quickly and easily configure rules to cut off unauthorized or abusive use of databases and minimize the risk of a data breach.
Data Risk Analytics Overview
To view an overview of what DRA can do for you, you can watch the video 👉 here. 👈 You will need to login to the community to watch it. In it you will find:
- A Short Introduction to DRA
- High level Use cases DRA solves
- Advanced Investigation & Tuning
- Tips for investigation
- Tips for tuning
- Tips for mitigating risk and threats
Learn More with Imperva Community
The Imperva Community is a great place to learn more about how to use Imperva cybersecurity technologies like WAF Gateway, Data Risk Analytics, Database Activity Monitoring and more to establish efficient, secure processes for enterprise networks. Rely on the expertise of Imperva partners, customers and technical experts.
Other Relevant Content